As a threat intel lead and riding all sort of new incidents in the past year, there is a change of attack vectors from adversary and cyber-criminals. The focus changes to human factors than complicated technical exploits which is a challenge for organizations to control. The purpose of this piece is to provide 8 highlights of what the individuals can focus to improve security hygiene and footprints on the internet.
MFA Everything
2022 is full of incidents pivoting around MFA bypass and social engineering attempts towards MFA token to breach into the system. Still, this is still a layer of defense from a bad guy from getting your legitimate credentials. Check all your software services and ENABLE MFA without any 2nd thought. When we are talking about Multi-Factor Authentication (MFA), there are 3 factors; what you know (password, PIN), what you have (security key, mobile phone auth token), and who you are (biometrics). A mix of at least 2FA or 3FA can prevent you from falling your valuable credentials into a bad guy, that leads into a major data breach.
Invest on Password Manager
Many people have more than a dozen web services and passwords that we used for it. It’s a bad idea to use the same key for all of them. It’s like you have 1 key that can open a front door to your house and a vault that keeps your valuables. It’s hard to remember and keep these Keys in a safe but accessible place. Do your research and choose a password manager but may not recommended LastPass due to its major data breach in 2022.
Monitor your email address from credential breach
Your personal or business email address are used for logging into may services. It is also likely to use as out-of-band authentication by some services such as an option to send out 2FA token. If your email with valid credentials is fell into a breach database in darkweb, it is a good exercise to reset password along with the other services that used the same password. For these reasons, it is a good idea to monitor your email address using website like HaveIBeenPwned or alerting from Firefox Monitor.
Invest on security key fob
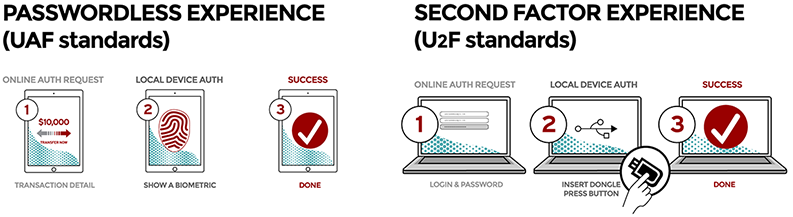
MFA makes user experience low but maintain good account security. FIDO Alliance proposes a new way to secure login with a good user experience by utilizing built-in security factors from your device such as biometrics and a security key fob that you can plugin or NFA to your deice and approve with a tap. The web services that supporting this new protocols is growing fast. Based on my personal experience. this is way faster and more convenient than punching 6 digits OTP token, SMS tokens and so on.
Stay Away from Badwares
If you want to save money and want to download pirated software and games from piratebay or other shady websites, please think twice. The consequences can be devastating since most of these software is modified with info-stealers and key-loggers that tracking your activities on the compromised deices. Basically, there is a chance of your credentials, credit card information and bank account can end up in another guy’s hand. The same applies for mobile apps and ONLY download apps from recognized repositories like Google Play or Apple Store.
Start using Egress Network Monitoring
I use a host-based firewall on my MacBook called Lulu. It is free and shout out to the developer, it is awesome. The best time to install is it after your OS is in a clean slate. Drop Lulu and whitelist the connections. Afterwards, all new connections are prompted for a quick review to allow or block. In case of unknown outgoing traffic, we can assume it as a malware of info-stealer tryting to establish conenction to its Command-and-Control (C2) server. It’s a bit annoying at first but can get used to it sooner or later. I found some Windows host-based Firewalls but can’t recommend due to lack of personal experience on these.
Avoid using devices with No Regular Security Patches
There are new vulnerabilities found by security researchers and adversary in a daily basis. At one point, legacy operating systems reach End of Life (EoL) and not going to receive any security patches. If we are still using these devices for processing sensitive applications such as mobile banking, there is a chance that adversary targeting these vulnerabilities can bypass control to gain access. So, better recycle these legacy devices or only use that don’t process sensitive information.
Understand Common Social Engineering Tactics
There are few common social engineering tactics used by attackers from phishing emails, SMS phishing, and luring you to become an insider threat of your organization with fake promises. Another trend in 2022 is OTP prompt bombing to you until you click ‘accept’ from plain frustration or to stop the annoyance. Be careful and think twice before approving or interacting something that out of your typical workflow. If there is impersonation of individuals in your organization and not certain of the request, call to check with the person directly. There is even approach of these fraudsters calling directly to your work line to request for installing malware or remote access software. These fraudsters are well trained and can speak native language.
These are some of the top concerns to improve your footprint and risk of being a victim of cyber attacks based on my observations from incidents from 2022. Stay safe and don’t be a patient zero that leads to compromise yourself, and your belonged organizations. Hope you find something useful in this piece.
